Benefits of app security analytics with Promon Insight™
Actionable, security-specific analytics
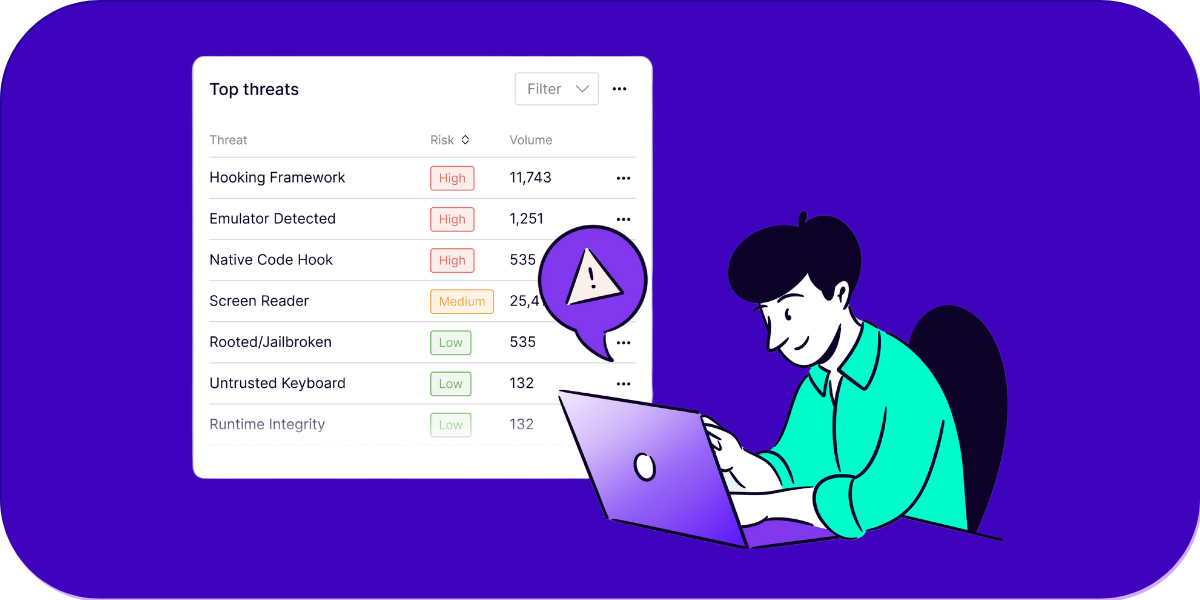
Identify and address security events like rooting, jailbreaking, runtime integrity breaches, and screen recording before they become critical. Promon Insight provides near-real-time, evidence-backed threat data that empowers your teams to act faster, focusing on security events unique to your mobile apps.

Easy executive reporting
Enable quick and transparent executive reporting for improved communication, faster decision-making, and more effective incident responses. Intuitive visuals make data easy to interpret for both technical and non-technical teams. Stakeholders gain clear insights into app health, user activity, and threat levels, with the ability to filter by operating systems, regions, device manufacturers, and more. Ready-made dashboards and seamless integration with existing SIEM tools enhance collaboration between security teams and business leaders.

Complete control and privacy
An on-premises implementation gives you full control over your client-server architecture. Customize configurations, manage security settings, and tailor the data flow to meet your needs. Privacy-focused by design, no PII from your users is sent to the Promon Insight Cloud. You can enrich data sets with PII using customizable features while maintaining complete control over personal data. This flexibility enables compliance with GDPR and CCPA, whether you include PII or not.

Reduce false positives
Sifting through countless alerts—many of them false positives—is a major challenge in app security. Promon Insight leverages deterministic and heuristic threat signals, enriched with evidence data, to reduce false positives and enhance detection accuracy. This means your security teams can focus on real, actionable threats rather than being distracted by irrelevant alerts.

Prevent fraud
Ensure compliance with regulations like PSD2 by continuously monitoring mobile app activity for signs of unauthorized or fraudulent transactions. Insight detects anomalies, such as suspicious geolocations, enabling swift identification and response. This safeguards sensitive payment data, reduces fraud risk, and helps meet high-security standards.

Prevent intrusion
Identify and quickly analyze suspicious activities and attack patterns across your entire install base. Stop intrusions before they escalate. Leverage security telemetry data to gain insights into unauthorized access attempts and fine-tune your intrusion detection and prevention systems. The result: an improved overall security posture.

Forensic analysis
Investigate security breaches with comprehensive forensic tools. Use app data to reconstruct events, identify the attack's root cause, evaluate its impact, and prevent future incidents. With the average cost of a data breach reaching $4.88 million in 2024, forensic analysis is essential to guard against future incidents.

Drive better security and business outcomes for your teams

C-Suite
- Keep track of risk reduction and incident prevention
- Gain visibility into app and regional risk profiles
- Benefit from geographic and revenue analysis

CISO, CIO, Security Engineer
- Trusted mobile-specific analytics
- Seamless integration with existing security layers
- Enables proactive, actionable security monitoring

Product Manager, Business Analyst
- Simplify complex data into accessible insights
- Enhance communication with intuitive reports
- Support quick, business-relevant decision-making

Mobile App Developer
- Hassle-free implementation
- Full configuration control
- Supports real-time monitoring during development
Promon Insight™ for your industry
Finance and banking
Detect and prevent fraudulent transactions in real-time, safeguard user authentication, and generate compliance reports with ease.
Gaming
Detect cheating attempts and protect virtual goods through detailed activity insights.
Streaming
Detect piracy and unauthorized access and understand device and regional risk profiles.
e-Commerce
Monitor and ensure transactions are secure against bot-driven credential-stuffing attacks.
Healthcare
Ensure data privacy and regulatory compliance, particularly for apps outside of HIPAA coverage, and prevent unauthorized data harvesting.
Frequently asked questions
1. What are security analytics?
Security analytics for mobile apps is the process of collecting and analyzing telemetry data from your applications to detect and respond to security threats. With security analytics, you can monitor the data on app or device performance, behavior, and security events to identify anomalies like unauthorized access or malware attacks. This enables you to proactively address vulnerabilities, enhance app security, comply with regulations, and deliver a safer experience for your users.
2. What is Promon Insight™, and how does it work?
Promon Insight™ is a mobile security analytics platform that collects data from mobile apps about the device, app health, and its operating environment. Here's how it works:
Insight Client (on the device): Resides within the Promon SHIELD-protected app and collects device and app usage data, encrypting the data before sending it. If the message can't be delivered immediately, it is stored in a write-ahead log and resent later.
Insight Agent (on the server): The server-side component that receives data from the Insight Client, decrypts it and forwards it to designated storage systems or analytics tools. The agent can be deployed on nearly any server and isn't tied to a specific runtime environment.
Insight Cloud: After the Insight Agent forwards the data, it is processed and stored in the Insight Cloud, where pre-built dashboards provide easy-to-understand analytics and benchmarking for administrators. These dashboards give organizations visibility into threats, app usage, and device performance.
Additionally, the Insight Agent can forward data to other APIs chosen by the organization, giving flexibility for custom integrations with existing analytics and visualization systems.
3. What data does Promon Insight™ collect?
The data collected will change over time with the evolving threat landscape and device and OS evolution. Initially, the data Insight collects will fall into the following categories:
- Install-base data: Device manufacturer and model, operating system, version and architecture, app name and version, SHIELD version, etc.
- Threat detections: jailbroken, rooted, untrusted keyboard, screen reader, emulator and hooking, etc.
- Evidence data: data that validates the level of evidence behind the detection.*
The data collected by Insight is carefully selected according to privacy laws such as the GDPR or CCPA. As Insight is based on the Promon Trust Architecture, custom data, which can be classified as PII data, will never be sent to the Insight Cloud. You will have the flexibility to send back any data you want without worrying about privacy or compliance.
*Future capability
4. What are the deployment options for Promon Insight™?
Promon Insight™ can be deployed on-premises or via the cloud, providing flexibility depending on organizational needs. The on-premises option ensures full control over data and security within the customer’s infrastructure, while the cloud deployment offers scalability, ease of management, and ready-to-go dashboards.
5. What types of threats can Promon Insight™ detect?
Promon Insight™ detects many mobile threats, including jailbreaking, rooting, debuggers, unauthorized access, emulator and hooking attempts, screen captures, screen recordings, screen readers, runtime integrity, virtual space, and more. It uses both deterministic and heuristic signals to provide comprehensive threat detection enriched with evidence-backed data to minimize false positives.
6. How long does it take to integrate Promon Insight™?
Promon Insight™ can be deployed and integrated into the app in minutes. Existing Promon customers only have to update their SHIELD® configuration to include Insight, which will automatically be included when the app is shielded. New customers benefit from the ease of implementation through Promon’s Shielder technology, implementing both SHIELD and Insight into the app in a matter of minutes, with no code changes required.
7. Can I use Promon Insight™ data in my own third-party tools, such as analytics or fraud prevention systems?
Promon Insight Agent can forward the data to your own third-party tools so you can leverage the power of mobile threat data to enhance your existing systems. As we add more connectors, we will enable quick and easy integration with popular third-party tools.
8. Can I add my own data to the data sent by Promon Insight™?
Yes, you can leverage Insight to add your own custom data elements to the data set. This allows you to add any custom data or data that can’t be collected by Promon due to privacy regulations and still benefit from its value in your own tools. By design, any custom data you add will never be sent to the Cloud component of Insight and will remain only under your control.