Over time, our industry has gotten a better grip on the mobile threat landscape. As it turns out, mobile security is all about data protection: Apps store our personal information, pictures, recordings, notes, account data, business information, location, and much more. They act as clients that connect us to services we use daily and as communications hubs that process every message we exchange with others. Compromise a person’s smartphone, and you get unfiltered access to their life. When we consider that mobile devices are more readily lost or stolen and mobile malware is on the rise, the need for data protection becomes even more apparent.
OWASP Top 10 security threats posed by mobile apps
The OWASP Mobile Top 10 is a list of the most common security risks affecting mobile applications.
M1: Improper credential usage
Attackers can gain unauthorized access to mobile apps by using hardcoded or improperly stored credentials or bypassing legitimate access requirements.
M2: Inadequate supply chain security
Attackers can introduce malicious code into the app to steal data, spy on users, or control the mobile device. They can also exploit vulnerabilities in third-party software libraries and hardcoded credentials.
M3: Insecure authentication/authorization
Attackers can fake or bypass authentication by directly interacting with the app's backend server or using mobile malware and botnets to log in as legitimate users.
M4: Insufficient input/output validation
Insufficient input/output validation in mobile apps can lead to vulnerabilities like SQL injection, command injection, and path traversal, compromising the mobile application.
M5: Insecure communication
Man-in-the-middle (MITM) attacks can intercept and manipulate communication to steal access tokens and API keys, bypassing implemented security measures.
M6: Inadequate privacy controls
Attackers can extract or manipulate personally identifiable information (PII) using overlay attacks, malware-infected apps, and keyloggers.
M7: Insufficient binary protections
App binaries can be attacked through reverse engineering and code tampering to uncover secrets, vulnerabilities, or insert malicious code.
M8: Security misconfiguration
Security misconfigurations, such as insecure default settings, weak encryption, and unprotected storage, can be exploited in mobile apps.
M9: Insecure data storage
Attack vectors include unauthorized access to device file systems, especially on rooted or jailbroken devices. Even on non-rooted or jailbroken devices, sensitive data can be stored outside the application (like storing pictures of a credit card in the photo library).
M10: Insufficient cryptography
Insecure cryptography in mobile apps can be exploited using various techniques, including cryptographic attacks and brute force.
Mobile app security must focus on how mobile apps handle, store, and protect sensitive information. It must cover the key components of the mobile app attack surface, including storage, cryptography, authentication and authorization, network communication, interaction with the mobile platform, code quality, and hardening against reverse engineering and tampering.

How to create a secure mobile app
Threat modeling helps you think like an attacker and gain a better understanding of how malicious threat actors can take advantage of your app’s vulnerabilities and exploit them.
“The first step to mitigate risks is to identify them. A threat modeling exercise is needed, looking at the function of the mobile application and the threats applicable during its operation”
Gartner

OWASP’s four question framework
The Open Worldwide Application Security Project (OWASP) recommends beginning the threat modeling process with a Four Question Framework:
- What are we working on?
- What can go wrong?
- What are we going to do about it?
- Did we do a good job?
The OWASP Mobile Application Security Verification Standard (MASVS) can help you and team to answer these questions, but also guide you to a suitable set of security controls for your mobile application to speed-up your threat modeling.
Speed up threat modeling with OWASP MASVS
The gold standard for mobile application security
What is the OWASP MASVS about?

OWASP Mobile Application Security Verification Standard (MASVS)
The OWASP Mobile Application Security Verification Standard (MASVS) has become the industry standard for mobile application security and is a valuable resource for developers, application owners, and security professionals. OWASP MASVS is the result of years of community effort and industry feedback. It provides a comprehensive set of clear and concise guidelines, best practices, and security controls that can be used to define and assess the security of mobile apps across various platforms (Android and iOS) in various use cases based on your industry-specific threats and mobile app architecture.
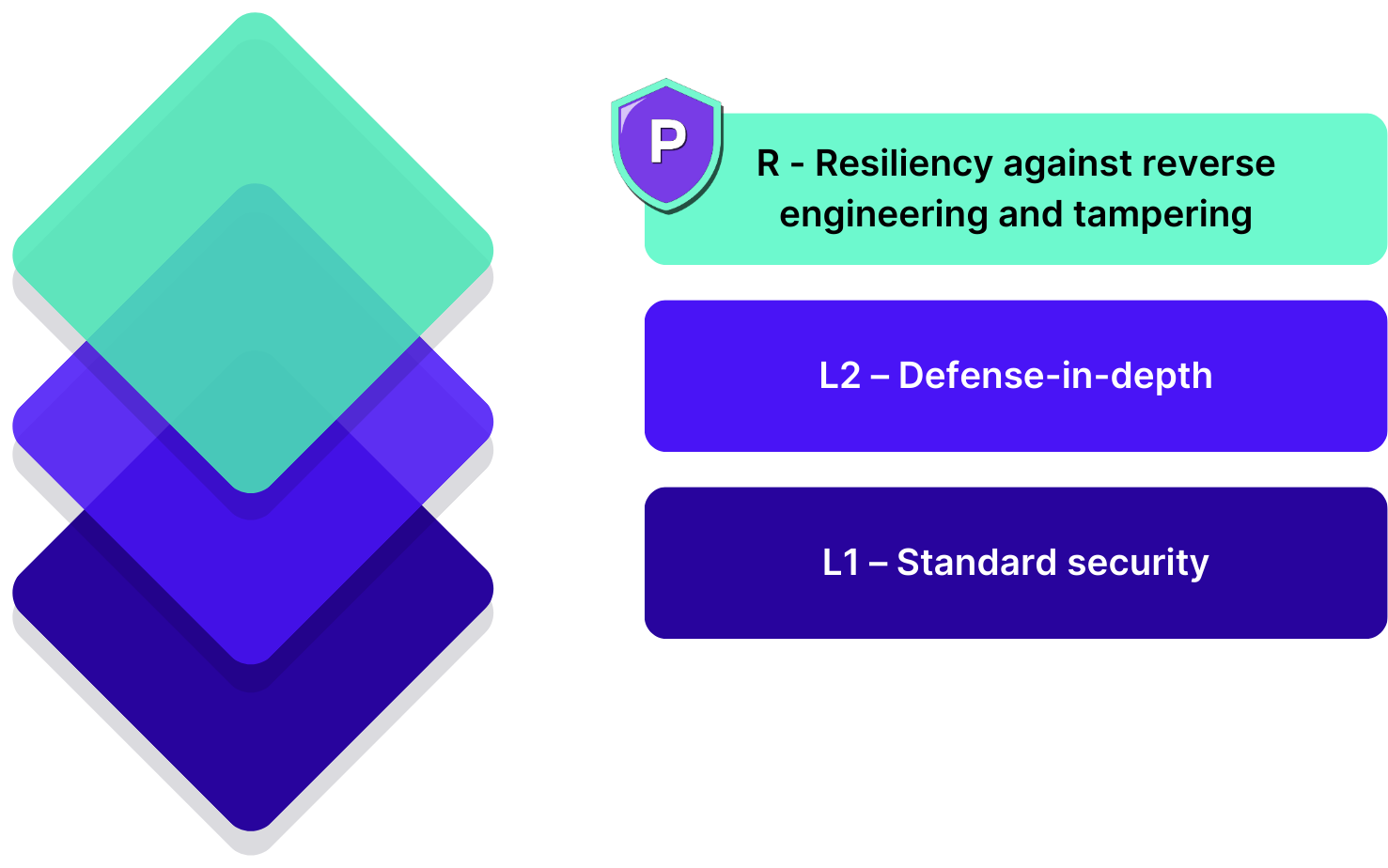
Three mobile app security testing profiles: Basic security, defense-in-depth, and resilience
OWASP MASVS provides three mobile app security testing profiles, each defining different security requirements and protection levels for mobile apps. This enables companies and developers to determine the appropriate security levels for their mobile apps and ensure that adequate security measures are implemented to guarantee the integrity and confidentiality of the data processed within the apps. Depending on the app’s use case and security requirements, the corresponding profiles and requirements can be selected or even combined.
MASVS Level 1: Basic security
MASVS Level 1 a good starting point for app developers who want to ensure their apps have at least a foundational level of security. It is typically suitable for apps that deal with lower-risk scenarios and minimal security needs.
MASVS Level 2: Defense-in-Depth
MASVS Level 2, also known as the “Defense-in-Depth”, is designed to address the security needs of mobile applications that require a higher level of protection. This profile is suitable for apps that handle sensitive data, operate in potentially riskier environments, or simply need to adhere to stricter security standards. It is highly relevant for mobile apps that handle personally identifiable information (PII), such as financial or healthcare data, or those that must meet strict regulatory requirements.
MASVS-RESILIENCE: Resilience against reverse engineering and tampering
MASVS-Resilience adds multiple security controls to the app, making it more difficult for attackers to reverse engineer and extract valuable intellectual property or sensitive data from it, which could result in:
Theft or compromise of valuable business assets such as proprietary algorithms, trade secrets, or customer data
Significant financial losses due to loss of revenue or legal action
Legal and reputational damage due to breach of contract or regulations
Damage to brand reputation due to negative publicity or customer dissatisfaction
Security goals for OWASP-MASVS Resilience
- Ensuring the trustworthiness and integrity of the platform on which the app operates
- Safeguarding the integrity of the intended app functionality
- Impeding analysis through static analysis by obscuring app functionality
- Preventing dynamic analysis and instrumentation that could enable potential code modifications by attackers during runtime
Which MASVS profile is applicable for your app?
| MAS L1 |
|---|
| No business assets |
| Low-risk sensitive data |
| No sensitive functionality |
| Example sensitive data: Name, email |
| Example apps: News (BBC News), Calendar (Google calendar) |
| MAS L1 + R |
|---|
| Business assets/logic |
| Low-risk sensitive data |
| No sensitive functionality |
| Example business assets: IP, ad revenue |
| Example apps: Ad-supported weather apps (Weather & Radar, Storm Radar) |
| MAS L2 |
|---|
| No business assets |
| Moderate/high risk sensitive data |
| Sensitive functionality |
| Example sensitive data: Location, payment information, access tokens, API keys, crypto keys, encrypted user data |
| Example sensitive functionality: Medical records, in-app purchases |
| Example apps: Messenger (WhatsApp), Health (MyDoctor), Sport (FitBit) |
| MAS L2 + R |
|---|
| Business assets/logic |
| Moderate/high risk sensitive data |
| Sensitive functionality |
| Example business assets: IP |
| Example sensitive functionality: Money transfers, in-app purchases |
| Example apps: Banking (ING banking to go), Insurance, Gaming (Pokemon GO), Entertainment |
Where does your app fit in?
Our application security experts can help assess how your app stores sensitive data, how exposed your business logic is, and more.

When to consider OWASP MASVS-Resilience against reverse-engineering and app-tampering?
To determine when it is essential to integrate MASVS-Resilience into your mobile app as the top layer of your security concept, consider the nature of your mobile app. If your mobile app includes any of the following assets, data, or functionality, OWASP recommends strengthening your mobile app against reverse engineering and app tampering. This should be done in addition to any basic or defense-in-depth security measures you may have already implemented.
| Sensitive business assets and logic | Sensitive data | Sensitive functionality |
|---|---|---|
| Intellectual property | Access tokens | Paid/premium features |
| Patents and copyrights on source code or algorithms | API keys | In-app purchases, subscriptions |
| Revenue streams | Sensitive PII, e.g. health or financial data | Money transfers |
| Upload functions such as medical records or other sensitive files |
Comply with OWASP MASVS-Resilience within minutes
Our app shielding software is offered as an on-premise SDK, requires minimal security knowledge, and takes care of the complexities of app security. Promon SHIELD™ can be integrated within minutes and works smoothly with every command line interface or your dev team’s favorite CI/CD tools.
Promon SHIELD™ is an app hardening technology that adds anti-reverse engineering and anti-tampering security features to your mobile app. At the same time, we help you to fulfil the OWASP MASVS-Resilience controls, going far beyond the requirements of the gold standard.
Features of Promon’s technology
| OWASP MASVS Resilience controls | Promon’s technology features |
|---|---|
| The app validates the integrity of the platform | – Emulator detection – Root & jailbreak detection – Detection and blocking of untrusted keyboards, keyloggers, screen readers, abusing the operating system’s accessibility services |
| The app implements anti-tampering mechanisms | – Runtime integrity checks – Code injection-prevention – Detection of hooking frameworks – Repackaging detection |
| The app implements anti-static analysis mechanisms | – Anti-debugging – Code obfuscation (Promon IP Protection Pro™) – Data encryption (Promon Asset Protection™) |
| The app implements anti-dynamic analysis techniques | – Debugger detection – Detection of reverse engineering tools |
