Promon security researchers have found proof of a dangerous Android vulnerability, dubbed ‘StrandHogg’, that allows real-life malware to pose as legitimate apps, with users unaware they are being targeted.
Research by: John Høegh-Omdal, Caner Kaya, & Markus Ottensmann
What’s the impact?
- All versions of Android up until Android 10 are affected*
- All top 500 most popular apps are at risk*
- Real-life malware is exploiting the vulnerability
- 36 malicious apps exploiting the vulnerability was identified*
- The vulnerability can be exploited without root access
When exploited by hackers
- They can listen to the user through the microphone
- Take photos through the camera
- Read and send SMS messages
- Make and/or record phone conversations
- Phish login credentials
- Get access to all private photos and files on the device
- Get location and GPS information
- Get access to the contacts list
- Access phone logs
*Lookout, a partner of Promon, confirmed that they have identified 36 malicious apps exploiting the vulnerability. Among them were variants of the BankBot banking trojan observed as early as 2017. *During testing, Promon researchers found that all of the 500 most popular apps (as ranked by app intelligence company 42 Matters) are vulnerable to StrandHogg. *All versions of Android affected, incl. Android 10* (note: the permission harvesting exploit is only from Android 6.0 and onwards).
BankBot: one of the most widespread banking trojans around, with dozens of variants and close relatives springing up all the time. BankBot attacks have been detected all over the world, in the U.S., Latin America, Europe and the Asia Pacific region.
How can hackers access all this?
Through dangerous permission harvesting
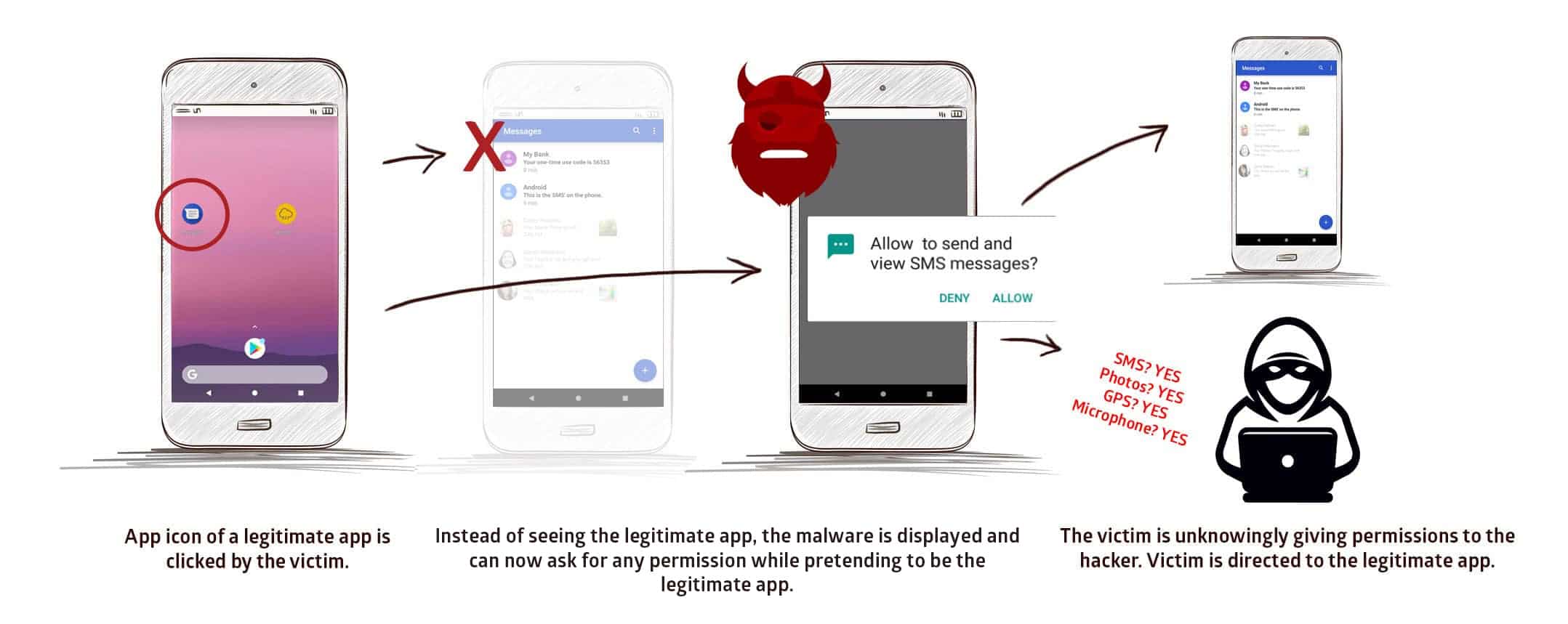
The vulnerability makes it possible for a malicious app to ask for permissions while pretending to be the legitimate app. An attacker can ask for access to any permission, including SMS, photos, microphone, and GPS, allowing them to read messages, view photos, eavesdrop, and track the victim’s movements.
The attack can be designed to request permissions which would be natural for different targeted apps to request, in turn lowering suspicion from victims. Users are unaware that they are giving permission to the hacker and not the authentic app they believe they are using.
…and powerful phishing attacks
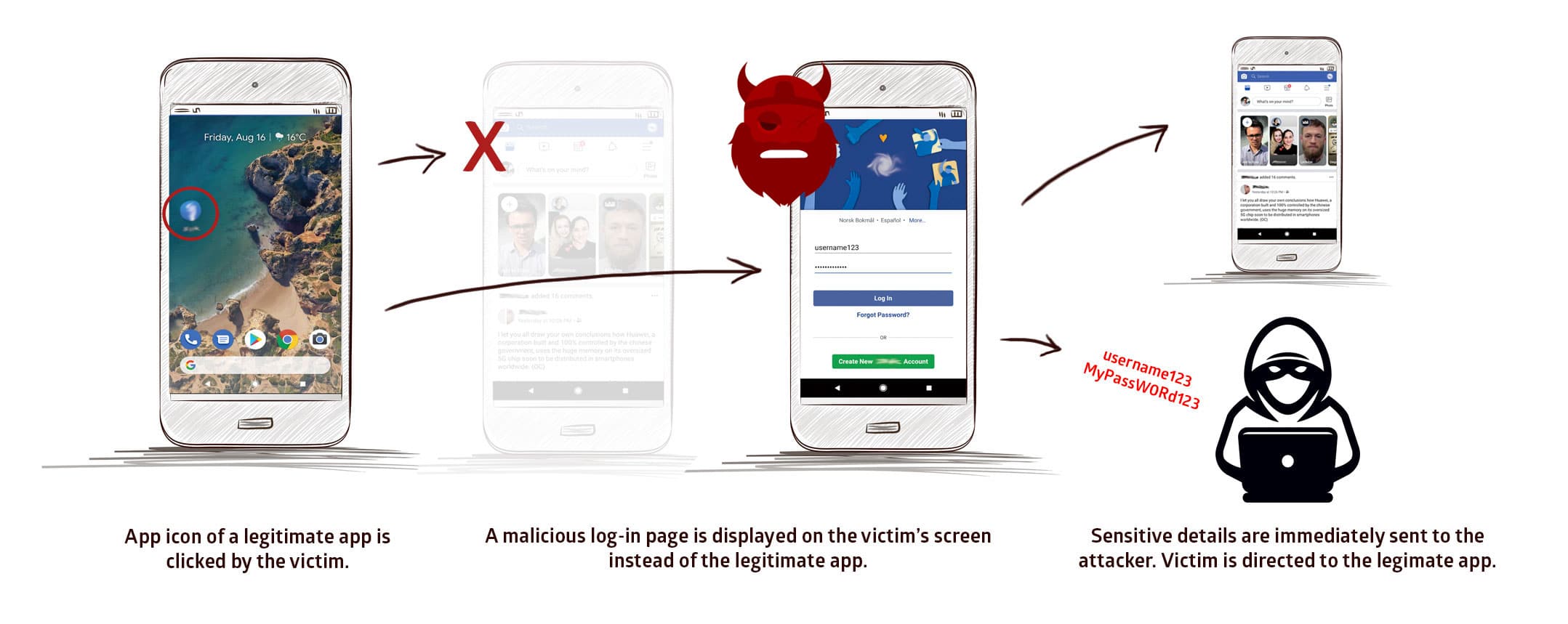
By exploiting this vulnerability, a malicious app installed on the device can attack the device and trick it so that when the app icon of a legitimate app is clicked, a malicious version is instead displayed on the user’s screen.
When the victim inputs their login credentials within this interface, sensitive details are immediately sent to the attacker, who can then login to, and control security-sensitive apps.
Would you notice if you were hacked this way?
The vulnerability explained
StrandHogg, unique because it enables sophisticated attacks without the need for a device to be rooted, uses a weakness in the multitasking system of Android to enact powerful attacks that allow malicious apps to masquerade as any other app on the device. This exploit is based on an Android control setting called ‘taskAffinity’ which allows any app – including malicious ones – to freely assume any identity in the multitasking system they desire.
Promon has conducted research on real-life malware that exploits this serious flaw and found all of the top 500 most popular apps (as ranked by app intelligence company 42 Matters) are at risk, with all versions of Android affected.
The vulnerability has been named by Promon as ‘StrandHogg’, old Norse for the Viking tactic of raiding coastal areas to plunder and hold people for ransom.
Promon’s study significantly expands upon research carried out by Penn State University in 2015, where researchers theoretically described certain aspects of the vulnerability. Google, at the time, dismissed the vulnerability’s severity, but Promon has tangible evidence that hackers are exploiting StrandHogg in order to gain access to devices and apps.
Malicious dropper apps frequently slip under Google’s radar
The specific malware sample that Promon analyzed did not reside on Google Play but was installed through several dropper apps/hostile downloaders distributed on Google Play. These apps have now been removed, but in spite of Google’s Play Protect security suite, dropper apps continue to be published and frequently slip under the radar, with some being downloaded millions of times before being spotted and deleted.
Demonstrative of the scale of Google Play’s issue with dropper apps, researchers recently reported that the malicious CamScanner app, a PDF creator that contains a malicious module, has been downloaded more than 100 million times.
Dropper apps / hostile downloaders: These are apps that either have or pretend to have the functionality of popular apps, such as games and utilities, but they also install additional apps to a device that can be malicious or steal your data.
“We have tangible proof that attackers are exploiting StrandHogg in order to steal confidential information. The potential impact of this could be unprecedented in terms of scale and the amount of damage caused because most apps are vulnerable by default and all Android versions are affected.”
Promon CTO Tom Lysemose Hansen
“Vikings were known to set up spy networks, with information on religious feasts and events, local customs and high-value personalities who could be ransomed being used when choosing the next area to attack. Cybercriminals are the modern-day Vikings, and we encourage individuals to be extra vigilant and for companies to ensure they have robust app protection in place.”
Promon CEO Gustaf Sahlman
Q&A
Has StrandHogg been abused in real-world cases?
Promon has tangible evidence that hackers are exploiting StrandHogg in order to gain access to devices and apps.
Promon identified the StrandHogg vulnerability after it was informed by an Eastern European security company for the financial sector (to which Promon supplies app security support) that several banks in the Czech Republic had reported money disappearing from customer accounts. At the time, this was covered (but not explained), in the Czech media. Promon’s partner gave Promon a sample of the suspected malware to investigate.
From here, through its research, Promon was able to identify the malware was being used to exploit a dangerous Android vulnerability (which it named ‘StrandHogg’). Lookout, a partner of Promon, also confirmed that they have identified 36 malicious apps exploiting the vulnerability. Among them were variants of the BankBot banking trojan observed as early as 2017.
Is the vulnerability patched by Google?
While Google has removed the affected apps, to the best of our knowledge, the vulnerability has not yet been fixed for any version of Android (incl. Android 10)
Does the StrandHogg exploit require root access?
This vulnerability can be exploited without root access.
What can a potential attacker do?
StrandHogg uses a weakness in the multitasking system of Android to enact powerful attacks that allows malware to masquerade as any other app on the device. Through permission harvesting, the malware can escalate its capabilities significantly and perform a wide range of damaging activities, such as:
- Listening to the user through the microphone
- Take photos through the camera
- Read and send SMS messages
- Make and/or record phone conversations
- Phish login credentials
- Get access to all private photos and files on the device
- Get location and GPS information
- Get access to the contacts list
- Access phone logs
Can malware that exploits StrandHogg be installed from Google Play?
The specific malware sample which Promon analyzed did not reside on Google Play but was installed through several dropper apps/hostile downloaders distributed on Google Play. These apps have now been removed, but in spite of Google’s Play Protect security suite, dropper apps continue to be published and frequently slip under the radar, with some being downloaded millions of times before being spotted and deleted.
Demonstrative of the scale of Google Play’s issue with dropper apps, researchers recently reported that the malicious CamScanner app, a PDF creator which contains a malicious module, has been downloaded more than 100 million times.
Which apps are affected by the vulnerability?
During testing we found that all of the 500 most popular apps (as ranked by app intelligence company 42 Matters) are vulnerable to StrandHogg.
Which Android versions are affected?
All versions, incl. Android 10. (note: the permission harvesting exploit is only from Android 6.0 and onwards)
When was this reported to Google by Promon?
Promon adheres to Google’s 90-day disclosure timeline. We submitted our report to Google this summer.
What makes the StrandHogg vulnerability unique?
StrandHogg is unique because it enables sophisticated attacks without the need for the device to be rooted. To carry out attacks, the attacker doesn’t need any special permissions on the device. The vulnerability also allows an attacker to masquerade as nearly any app in a highly believable manner.
Can I detect if someone exploits StrandHogg on my device?
Generally speaking, no. There’s no effective block or even reliable detection method against StrandHogg on the device itself. Aware users may notice discrepancies during the use of their device, including:
- An app or service that you’re already logged into is asking for a login.
- Permission popups that does not contain an app name.
- Permissions asked from an app that shouldn’t require or need the permissions it asks for. For example, a calculator app asking for GPS permission.
- Typos and mistakes in the user interface.
- Buttons and links in the user interface that does nothing when clicked on.
- Back button does not work like expected.
Closing the app from the Recents screen can be effective – however, it is possible for an attacker to also circumvent this. It’s possible to connect the phone via USB, and running adb shell dumpsys activity activities which will give you a technical list of all visible screens, and what task they currently are in, along with which app they actually belong to. However, this method requires some technical knowledge and knowing what to look for.
Can I detect if someone exploits StrandHogg against my own app?
There are some basic task information that can be retrieved through the Android SDK. However, due to the nature of tasks, activities (and thus entire apps) that are not in the foreground may not even be running. Consequently, your app might get hijacked without even running.
There are no callbacks or broadcasts in Android that could give you a notice when your task is hijacked, so you would have to be running a monitoring service in the background continuously. It’s worth noting that a malware/attacker does not need to modify, change or touch your app in any way in order to attack it. As such, monitoring your own app for changes, repackaging/signature checks etc is ineffective in blocking StrandHogg.The developer of a benign app can set the task affinity of all activities to “”(empty string) in the application tag of AndroidManifest.xml to indicate the activities of the benign app do not have an affinity to any task. This mitigates the risk only to some extent.
Why is it called "StrandHogg"?
The vulnerability has been named by Promon as ‘StrandHogg’, old Norse for the Viking tactic of raiding coastal areas to plunder and hold people for ransom.
Can I use the StrandHogg logo?
The logo is free to use, and rights are waived via CC0. Download SVG and PNG.
In more detail
We have seen malware utilizing the StrandHogg vulnerability as a main strategy, for the first time. The malware itself did not reside on Google Play but was installed through several Hostile Downloaders, i.e. malicious apps that are distributed on Google Play.
The exploits described above works when a malicious app sets the taskAffinity on one or more of its activities to match the packageName of any third-party app. Then, by either combining with allowTaskReparenting=”true” in manifest, or by launching the activity with intent-flag of Intent.FLAG_ACTIVITY_NEW_TASK the malicious activity will be placed within and on top of the target’s task.
Thus the malicious activity hijacks the target’s task. The next time the target app is launched from Launcher, the hijacked task will be brought to the front and the malicious activity will be visible.
The malicious app then only needs to appear like the target app to successfully launch sophisticated attacks against the user. It is possible to hijack such a task before the target app has even been installed.

Disguising an attack
StrandHogg is centered around activities, and their movements, between tasks in the multitasking handling system of Android.
By launching two (or more) activities at the same time with android.app.Activity#startActivities(android.content.Intent[]),
it’s possible to simultaneously launch both the attack and something that appears innocent.
In the background, the attack prepares and hijacks the target before the user even sees anything on the screen. Other than some minor flickering on certain devices, the user will only see the benign activity and will have no idea that malicious activity has taken place.
If we look at the output of adb shell dumpsys activity activities we can see the attack activity is already in position, lurking until the next time the app is launched. And indeed, the next time the victim-app is launched (by clicking its icon), we see the attacker instead of the victim.


allowTaskReparenting
There’s also an attribute called allowTaskReparenting which, when used, will not immediately transfer the attacker activity onto its target. Instead, the next time the target task is launched, the Android operating system evaluates all tasks and activities, and looks for activities marked with this attribute and moves them before launching the related task.
Meanwhile, every activity has information about their own tasks and which taskID they belong to. The attacking activity can use this information to understand what task it resides in, and then just in time show either benign or malicious content on the screen accordingly.

Task monitoring
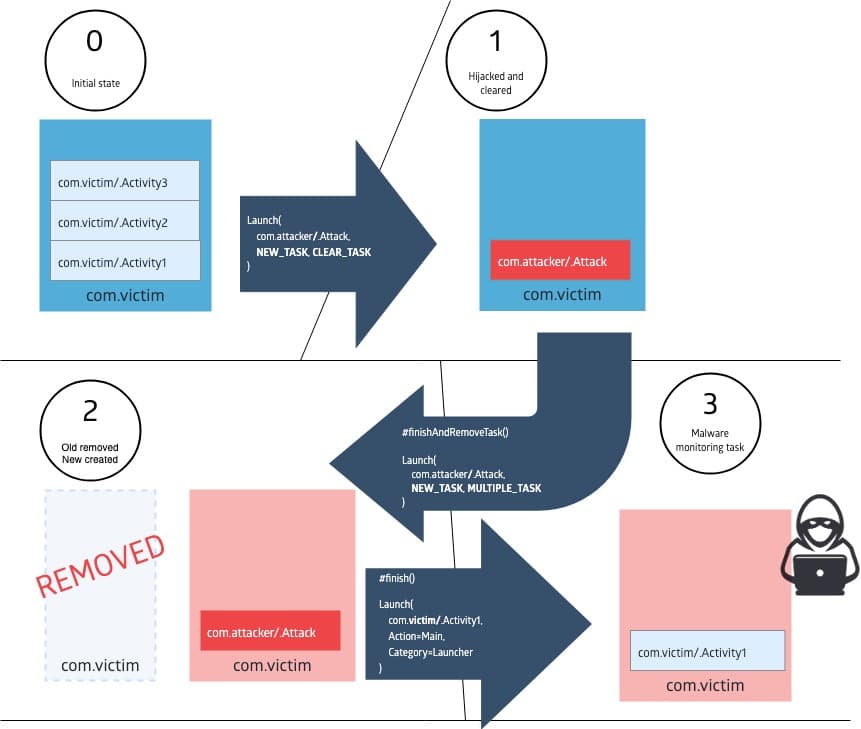
What is particularly egregious is that the attacker can gain significant control over the victim’s task. By combining with Intent#FLAG_ACTIVITY_NEW_TASK and Intent#FLAG_ACTIVITY_CLEAR_TASK, the attacker first clears out the target task, and then gets launched into it.
That activity can then finish the target task with android.app.Activity#finishAndRemoveTask, and launch a new task with the same affinity with Intent#FLAG_ACTIVITY_NEW_TASK and Intent#FLAG_ACTIVITY_MULTIPLE_TASK and thus create a new target task guaranteed to be under the attacker’s control. After that, the attacker can launch the victim’s actual launcher activity, and let the victim’s app run its course as usual.
Meanwhile, because the attacker still retains control over the victim’s task, it now has a lot more information about the state of the target. It may then intercept and inject a phishing activity deep in the flow of the target application, in a place that is much more natural to the user and flow of the target app.