How application hardening can be used to detect cyber attacks, prevent them using application hardening, and the benefits of threat intelligence.
In 2014 the number of mobile computing devices in use surpassed that of desktop machines worldwide. In 2017 there were more than 4.5 billion mobile phone users in the world. Nearly 90-percent of usage on mobile phones and tablets occurs through apps. The prevalence of the Internet of Things and increasing use of personal devices in vulnerable sectors have made the need for application hardening urgent.
Bring your own device
The dynamic state of mobile app security is of special concern in the healthcare and financial sectors. It is also of concern for any industry that supports Bring-Your-Own-Device (BYOD) policies within their organizations or offers consumer-facing mobile apps.
BYOD is a practice in which institutions permit employees and business partners to use their own mobile applications devices to perform their duties. The approach exposes enterprises to data breaches through the lack of uniform and frequent cybersecurity protections to applications and data residing on mobile devices.
Internet of things
Users of IoT (Internet of Things) devices face even greater cyber dangers. Gartner, a technology sector research firm, predicts that by the end of 2017 there will be more than eight billion of the internet-connected gizmos in use globally.
The researcher foresees that organizations and consumers will have twice that many of the “things” in use by 2020. Many IoT device manufacturers rely on out-of-date versions of the Windows OS to run their machines.
Most IoT device manufacturers do not provide security patches to protect the apps that drive their electronics.
Application hardening
A significant development in mobile app security, desktop security and IoT applications is application hardening. Application hardening technology “hardens” apps against cyber intrusions.
The technology, however, is not a replacement for security measures integrated into app development at the outset of development.
There are specific instances in which application hardening should be a required part of every organization’s mobile app security practices of detection, prevention and prediction of cyber attacks on devices.
Three fundamental aspects of mobile app security
Organizations implement application hardening to protect apps on mobile devices like smartphones and tablets, desktop and laptop machines against intrusion, tampering and reverse engineering.
However, the market for mobile devices is growing rapidly while the sales of laptop and desktop machines continue to deteriorate. The trends are forcing IT and cybersecurity professionals to focus their attention on protecting the smaller, less well-defended electronics upon which consumers and organizations have come to rely.
Enterprises and individuals need also to be concerned about the cybersecurity vulnerabilities that the Internet of Things (IoT) present.
The expansion and staggering diversity of mobile and IoT devices are contributing to what cyber security professionals call an increasing “attack surface” for cybercriminals. An attack surface involves any and all the vulnerabilities an operating system or software on devices offer a hacker to intrude on the operation of a computing device.
Healthcare sector most vulnerable
The healthcare sector, however, is one of the most vulnerable to cyber attacks. Healthcare delivery lies at the intersection of mobile device usage and IoT implementation. Doctors and administrators are more frequently carrying around tablet computers to manage patient care.
Furthermore, medical devices like pacemakers, defibrillators, and insulin pumps are under threat from hackers. Patient records that cybercriminals can access through enterprise networks are not only at risk, but a threat to patient health. Any combination of devices associated with a patient may be manipulated with malicious intent.
No matter the organization, sector or device, IT professionals must adhere to three fundamental aspects of mobile app security: detecting cyber attacks, preventing intrusions, and predicting when malware attacks an application.
1. Detecting cyber attacks
The most significant challenge to protecting against hackers is that the overwhelming majority of mobile and IoT devices exist outside the fortress of enterprise firewalls.
Users of mobile and IoT devices — even those that are part of corporate BYOD programs — cannot be assured that product makers and employers will roll out current and adequate protections for applications and data residing on the devices.
Moreover, neither can enterprises and vendors confirm that users would apply software security patches promptly.
The most effective application hardening products offer Privilege escalation detection. Attackers can grant themselves super-user access to machines and networks by taking advantage of vulnerabilities in operating systems.
On mobile devices, the approach typically used to gain deeper control is called Jailbreaking or Rooting.
Jailbreaking/Rooting involves hackers subverting the natural flow of fundamental operations to gain complete control of a device. Jailbreaking/Rooting obliterates the controls that operating system makers have placed on their products to support software applications and services on a device.
Jailbreaking and Rooting occur at the “root” — or most basic — level of operating systems. Privilege escalation detection alerts app custodians whether Malware has compromised a device’s operating system at the root level.
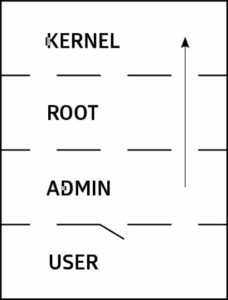 The arrow represents a rootkit gaining access to the kernel, and the little gate represents normal privilege elevation, where the user has to enter an Administrator username and password. Source: Wikipedia
The arrow represents a rootkit gaining access to the kernel, and the little gate represents normal privilege elevation, where the user has to enter an Administrator username and password. Source: Wikipedia
Additionally, Integrity checks can detect whether an app has been altered. Integrity checks can involve a variety of validations, such as checksums or an audit of the inventory of libraries and calls included in the application.
Two other must-have features that make application hardening valuable are Device Binding and Anti-Debugging/Emulation.
Device Binding securely links an authorized user to his authorized device(s). It is important in terms of preventing cloning or repurposing of cryptographic keys.
The Anti-debugging/Emulation detection can identify ongoing attacks to a device. It also provides protection against the use of debug tools to reverse-engineering applications.
2. Prevention
One of the main prevention features that application hardening provides is obfuscation. This technique means transforming the software program into code that’s difficult to disassemble and understand.
However, the program still has the same functionality as the original. Additionally, the software becomes impervious to reverse-engineering. Obfuscation hides the vulnerabilities of software to prevent theft and safeguard its intellectual property.
Keylogging Prevention / Detection, involves protecting against a hacker’s attempt to record the keystrokes entered onto mobile devices.
Prevention includes techniques to harden the application against Man-in-the-Middle (MITM) attacks. MITM assaults on devices occur through proxies (like cafes, hotels, and even places of work) that intercept a device’s HTTP(S) internet traffic.
Attackers can provide fake certificates of websites and present fake chains of trust that hide their presence and intentions.
Further, an essential aspect is authentication hardening. To ensures a simple and secure user authentication process, techniques such as Keylogging Prevention / Detection, which involves protecting against a hacker’s attempt to record the keystrokes entered onto mobile devices, should be a part of the feature set.
Hackers can easily analyse software to gain access to security keys. This is compounded by the trend toward operating secure software on open platforms. These operating systems should always be considered as compromised.
Whitebox cryptography dissolves keys into the programming code and obscures algorithms, even at runtime. The technique keeps keys safe even when an attacker has complete access to the device on which the cryptographic functions are executing.
3. Prediction
Cybersecurity is still a long way from predicting just when and what threats will strike. The best that many vendors of security software can do is to ensure their threat intelligence is up to date and that the databases they use to detect threats on local machines are current.
Some software is equipped with the ability to take advantage of data analytics and threat intelligence and includes calculated anticipation of cyber attacks based on trends and reports “in the wild” — that is, outside the immediate domain of the application.
Runtime Application Self-Protection (RASP) is a security technology that provides adaptive functionality to applications. Gartner defines RASP as “a security technology that is built or linked into an application or application runtime environment. The technology “is capable of controlling application execution and detecting and preventing real-time attacks.”
This security add-on provides self-protection abilities to services and apps. With RASP the app is self-protecting and protection are restricted to the application only, and the application can operate securely even on highly infected devices.
Easy to implement
Application hardening technology should only require a few minutes for your developers to install. Typically, application hardening kits include integration tools to facilitate application hardening.
Application hardening technology should only require a few minutes for your developers to install.
Similarly, many application hardening packages enable application developers to integrate their products through a Software Developer Kit (SDK) included with the shielding solution. Once secured, the applications are immediately ready for distribution via public or enterprise app stores.
Though application hardening still does not offer a predictive capability to cybersecurity measures, it presents formidable detection and prevention measures.
Moreover, with the number of mobile and IoT devices fast exceeding the number of human beings on planet Earth, the technology is proving to be one of the most effective and intelligent defences against mobile cybercrime.




